Cisco AP Flash corruption issues.
Wednesday, October 4, 2023
Cisco AP Flash corruption issues.
Tuesday, September 12, 2023
Thursday, April 20, 2023
Cisco WLC - Issues with APs Joining the Controller and Upgrading Firmware After 12/4/2022
Any IOS-based AP (1700/2700/3700/1570) downloading a new image from WLC running any version after December 4th 2022.
The AP can leave and re-join any WLC after Dec 4th 2022 provided it does not have to download a new image, if it has to download a new image (regardless of the version, 9800 IOS-XE or AireOS), it will fail.
For any WLC that has APs stuck in the downloading state:
- Disable Network Time Protocol (NTP) on the WLC and manually set the WLC date/time to a date before December 2, 2022. The Cisco IOS AP will then be able to download and validate the image, install the new image, and join the controller. Once the AP has joined the controller, NTP can be re-enabled on the controller to assume the correct date and time.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwd80290
https://www.cisco.com/c/en/us/support/docs/wireless/aironet-700-series-access-points/218447-ios-ap-image-download-fails-due-to-expir.html
https://www.cisco.com/c/en/us/support/docs/field-notices/725/fn72524.html
Wednesday, June 15, 2022
Autohotkey (AHK) Reformat MAC Addresses
Here is an AHK script to reformat MAC addresses. It takes a MAC address from the clipboard with :, -, ., or no separators and reformats it into several options each on their own line in the clipboard.
Output:
AA:AA:BB:BB:CC:CC
AA-AA-BB-BB-CC-CC
AAAABBBBCCCC
AAAA.BBBB.CCCC
Script:
;reformats MAC addresses. Press ALT+Shift+M
!+m::
Clipboard := StrReplace(Clipboard,"-","")
Clipboard := StrReplace(Clipboard,":","")
Clipboard := StrReplace(Clipboard,".","")
sleep 10
var1 := Clipboard
var2 := RegExReplace(Clipboard,"(?<!^.)(..)(?=[^$])","$1:")
var3 := RegExReplace(Clipboard,"(?<!^.)(..)(?=[^$])","$1-")
var4 := RegExReplace(Clipboard,"(?<!^.)(....)(?=[^$])","$1.")
var5 = %var2%`n%var3%`n%var1%`n%var4%
Clipboard := var5
return
Wednesday, May 11, 2022
Windows ARP Scan Utility
ARP scanning a subnet in Windows can be done with Nmap but some AV/security utilities don't like Nmap and it's a bit heavy. arp-scan-windows can be used as a simple standalone program to scan a subnet.
Link: https://github.com/rsweet2/arp-scan-windows
Wednesday, March 9, 2022
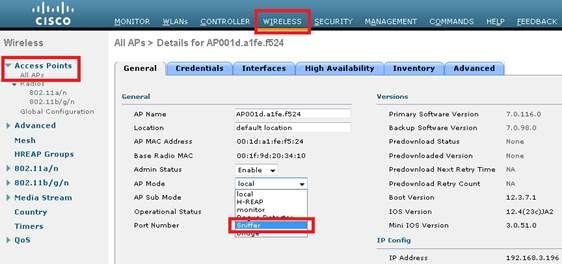
Cisco WLC - Use AP as a Sniffer
And send traffic to remote wireshark.
https://www.cisco.com/c/en/us/support/docs/wireless-mobility/80211/200527-Fundamentals-of-802-11-Wireless-Sniffing.html#anc12
Wireshark Capture filter - host 10.1.1.3 more info
1) WLC / AP side
Here are the steps in order to collect a trace using a sniffer mode LAP
- Configure the AP in Sniffer mode:
The AP will reboot and it will not be able to serve clients.
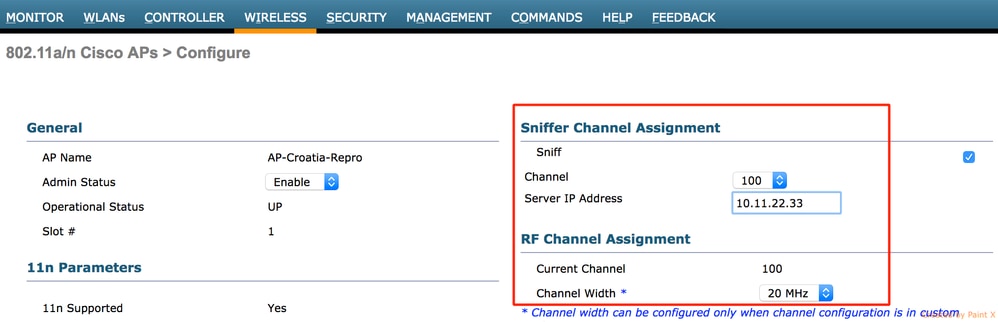
- Once the AP has re-joined the WLC, configure the radio of the AP (802.11b/g/n or 802.11a/n):
- specify the sniffer IP address
- select the channel
- enable sniffing
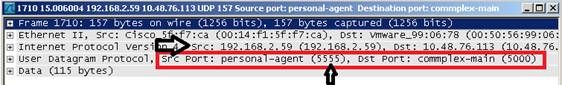
- The sniffer will receive the 802.11 traffic encapsulated using the airopeek protocol, from the WLC management IP address with source port UDP/5555 and destination UDP/5000
2) Sniffer side: Wireshark
If using Wireskark to receive the traffic, follow the steps below:
- Set the capture options to receive only traffic coming from the sniffing AP. If you set the filter only for port UDP 5000, you will miss IP fragments in the capture if the AP has to fragment the packet (which will happen if it sniffed a 1500 bytes long frame to which it needs to add PEEKREMOTE encapsulation):
This filter is optional but strongly recommended as it excludes all the non-wireless related traffic from the capture. Consider that the WLC sends traffic to a UDP port there’s no application listening on the sniffer side; this results in having a ICMP port-unreachable response for each packet received from the WLC.
Although this is expected, the filter above helps to exclude also this traffic which is useless and so it can only cause the trace to be bigger and more difficult to read.
- Then, start the capture:
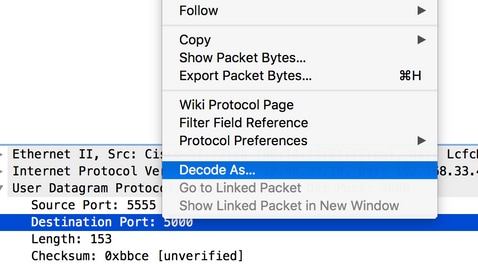
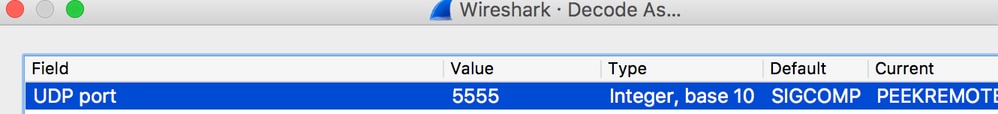
- The captured traffic has to be “decoded as..” PEEKREMOTE in order to be able to see the 802.11 traffic:
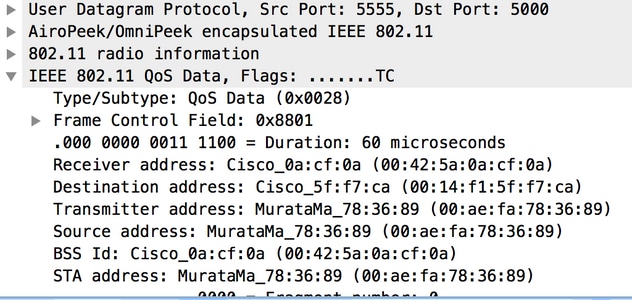
- The 802.11 traffic will now be visible:
The RF info shown above (e.g. the channel, signal strength, noise..) are added by the AP.
Monday, October 25, 2021
Cisco CUE Service Module - Show console output without logging in
test service-module integrated-Service-Engine 0/0 console
let's you see the most recent console output without needing to actually log in.
https://www.cisco.com/c/en/us/td/docs/voice_ip_comm/unity_exp/rel8_6/install/CUE_86_install/boothelp.html
Problem - No Session
You are unable to open a session to the CUE module or you do not see any output on the console.
Solution
You can use this command in order to check the console messages on the CUE module without the need to open a session to it:
Router# test service-module service-engine slot/unit console
By default, this command displays the most recent 80 lines stored in the console buffer. However, it is possible to specify an offset of greater or less than 80, or to view all the messages stored in the console buffer with this command:
Router# test service-module service-Engine slot/unit console ?
<1-20456> Offset into console buffer
all Entire console buffer
Thursday, October 14, 2021
Thursday, June 24, 2021
Sonicwall Multiple WAN Subnets Configuration
Configuration information for configuring multiple WAN interfaces
Should work for Comcast EDI (Fiber) circuits
https://www.sonicwall.com/support/knowledge-base/configuring-multiple-wan-subnets-using-static-arp-with-sonicos-enhanced/170503911164326/
https://www.carlc.com/modules/Wordpress_Blog/configure-sonicwall-router-for-comcast-business-fiber-ethernet-multiple-ip-segmentsranges/
Pretty sure this should work too - assigning it to a DMZ zone http://starforce.cyou/
Thursday, June 3, 2021
Sonicwall Firewall Configuration Decode
base64 -d -i "SonicWallConfig.exp" | sed 's/&/\n/g' > SonicwallConfig.txt
https://www.sonicwall.com/support/knowledge-base/how-to-get-the-configurations-of-the-firewall-based-on-the-exporting-exp-file/170503330364045/
Friday, May 21, 2021
Sonicwall Firewall - Gen 7 Diag Page
To access the diag page on gen 7 firewalls go to
/sonicui/7/m/mgmt/settings/diag
e.g. https://10.1.1.1/sonicui/7/m/mgmt/settings/diag
Friday, April 2, 2021
Get DTMF to Work Between a Switchvox PBX and Vega Gateway
Change the Switchvox PBX to use Inband DTMF in the SIP provider settings for the Sangoma gateway provider.
The default on the PBX is RFC4733 and the default on the gateway is RFC2833 so I'm not sure why this is required.
This worked on a Vega 60Gv2 gateway.
Wednesday, March 24, 2021
Find hardware version of Raspberry Pi from the command line
Monday, March 15, 2021
Windows Server Activation
Several Windows Server 2019 installs wouldn’t let me activate them normally. To do it, launch an elevated command prompt and use this command -
cscript c:\windows\system32\slmgr.vbs /ipk <product-key>
Thursday, February 25, 2021
Cisco WLC AP Certificate Ignore
For 7.4.140.0 and later:
(WLC)>config ap cert-expiry-ignore {mic|ssc} enable